Read more of this story at Slashdot.

Enlarge / Cinnamon (Photo by Hoberman Collection/Universal Images Group via Getty Images) (credit: Getty | Hoberman Collection)
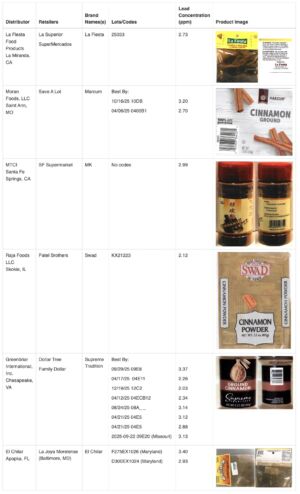
Six different ground cinnamon products sold at retailers including Save A Lot, Dollar Tree, and Family Dollar contain elevated levels of lead and should be recalled and thrown away immediately, the US Food and Drug Administration announced Wednesday.
The brands are La Fiesta, Marcum, MK, Swad, Supreme Tradition, and El Chilar, and the products are sold in plastic spice bottles or in bags at various retailers. The FDA has contacted the manufacturers to urge them to issue voluntary recalls, though it has not been able to reach one of the firms, MTCI, which distributes the MK-branded cinnamon.
The announcement comes amid a nationwide outbreak of lead poisoning in young children linked to cinnamon applesauce pouches contaminated with lead and chromium. In that case, it's believed that a spice grinder in Ecuador intentionally added extreme levels of lead chromate to cinnamon imported from Sri Lanka, likely to improve its weight and/or appearance. Food manufacturer Austrofoods then added the heavily contaminated cinnamon, without any testing, to cinnamon applesauce pouches marketed to toddlers and young children across the US. In the latest update, the Centers for Disease Control and Prevention has identified 468 cases of lead poisoning that have been linked to the cinnamon applesauce pouches. The cases span 44 states and are mostly in very young children.

Apple’s iOS 17.4 update is now available, introducing new emoji and a cryptographic security protocol for iMessage, alongside some major changes to the App Store and contactless payments for the iPhone platform in Europe. Apple is making several of these changes to comply with the EU’s Digital Markets Act (DMA), a law that aims to make the digital economy fairer by removing unfair advantages that tech giants hold over businesses and end users.
iOS 17.4 will allow third-party developers to offer alternative app marketplaces and app downloads to EU users from outside the iOS App Store. Developers wanting to take advantage of this will be required to go through Apple’s approval process and pay Apple a “Core Technology Fee” that charges 50 euro cents per install once an app reaches 1 million downloads annually.
iPhone owners in the EU will see different update notes that specifically mention new options available for app stores, web browsers, and payment options.
The approval process may take some time, but we know that at least one enterprise-focused app marketplace from Mobivention will be available on March 7th. Epic is also working on releasing the Epic Game Store on iOS in 2024, and software company MacPaw is planning to officially launch its Setapp store in April.
Fortnite is coming back to iOS in Europe this year!
— Epic Games Store (@EpicGames) January 25, 2024
Via our soon to launch @EpicGames Store for iOS thanks to new rules in Europe via the new Digital Markets Act (DMA), stay tuned for more details. https://t.co/7nOa2lcdhN
iOS 17.4 allows people in the EU to download alternative browser engines that aren’t based on Apple’s WebKit, such as Chrome and Firefox, with a new choice screen in iOS Safari that will prompt users to select a default browser when opened for the first time. While no browser alternatives have been officially announced, both Google and Mozilla are currently experimenting with new iOS browsers that could eventually be released to the public.
Apple is also introducing new APIs that allow third-party developers to utilize the iPhone’s NFC payment chip for contactless payment services besides Apple Pay and Apple Wallet in the European Economic Area. No alternative contactless providers have been confirmed yet, but users will find a list of apps that have requested the feature under Settings > Privacy & Security > Contactless & NFC.
While Apple previously revealed it was planning to drop support for progressive web apps (PWAs) in the EU to avoid building “an entirely new integration architecture” around DMA compliance, the company now says it will “continue to offer the existing Home Screen web apps capability” for EU users. However, these homescreen apps will still run using WebKit technology, with no option to be powered by third-party browser engines.
Outside of its DMA obligations, Apple’s iOS 17.4 update adds some new, widely available features that can be enjoyed globally. The Podcasts app is adding auto-generated audio transcripts for English, French, German, and Spanish-language podcasts, which can be searched for specific phrases or words to go directly to the corresponding point in the episode. A new cryptographic protocol for iMessage, known as PQ3, is also included in the iOS 17.4 update, supposedly bolstering end-to-end messaging encryption against potential quantum computing attacks. No such attacks have been disclosed, but Apple is laying the groundwork to prepare for such an eventuality.
Siri has a new option to read incoming messages in any Siri-supported language, which includes Spanish, French, German, Chinese, and more. Over 100 new emoji — such as a lime, broken chain, brown mushroom, and nodding / shaking heads — are also being added following the Unicode 15.1 update last September.
iPhone 15 devices will now display more battery-related information under the Battery Health settings, including cycle count, manufacture date, and when the battery was first used. And finally, the music recognition feature introduced in iOS 14.2 will now let users add identified songs to their Apple Music library and playlists.
iOS 17.4 is compatible with the same range of iPhone models as iOS 17, going back to the iPhone X range and second-generation iPhone SE. The rollout may be gradual, but you can check if it’s available on your device by heading into Settings > General > Software Update.

For some Apple Vision Pro buyers, the honeymoon is already over.
It’s no coincidence that there’s been an uptick on social media of Vision Pro owners saying they’re returning their $3,500 headsets in the past few days. Apple allows you to return any product within 14 days of purchase — and for the first wave of Vision Pro buyers, we’re right about at that point.
Comfort is among the most cited reasons for returns. People have said the headset gives them headaches and triggers motion sickness. The weight of the device, and the fact that most of it is front-loaded, has been another complaint. Parker Ortolani, The Verge’s product manager, told me that he thought using the device led to a burst blood vessel in his eye. At least one other person noted they had a similar experience with redness. (To be fair, VR headset users have anecdotally reported dry eyes and redness for years.)
“Despite being as magical to use as I’d hoped, it was simply way too uncomfortable to wear even for short periods of time both due to the weight and the strap designs. I wanted to use it, but dreaded putting it on,” says Ortolani, who also posted about returning the device.
“It’s just too expensive and unwieldy to even try to get used to the constant headaches and eye strain I was experiencing. I’ll be back for the next one.”
Can’t wait to return the Vision Pro, probably the most mind blowing piece of tech I’ve ever tried.
— Rjey (@RjeyTech) February 14, 2024
Can’t deal with these headaches after 10 minutes of use though.
This isn’t surprising. Every human body is unique, which is a problem when you’re scaling wearable production for the mass market. Comfort is inevitably sacrificed — and it affects people disproportionately. With smartwatches, it often boils down to the size and weight of the case compared to your wrist. With smart rings, it’s the size of your finger. Many people are unfortunately between sizes or have issues with finger swelling. For smart glasses and headsets, having a low nose bridge can mean the device just slips off your face or fails to adequately block out light.
But the hardware isn’t the only issue. Another common complaint is the Vision Pro doesn’t offer enough productivity relative to the price. One user noted on Threads that looking at Figma screens made them feel dizzy but that the device also wasn’t applicable to their work. Another engineer wrote on the social media platform X that the “coding experience failed to convince [him]” and focusing issues caused headaches.
“If I’m not using this for productivity, and if I don’t love it for entertainment, and if there aren’t enough games to play on it - I just can’t justify keeping it,” one Reddit user wrote.
Two hours after unboxing my Apple Vision Pro and using it, I decided to box it back up again and return it. It's quite cool, but there's nothing in it for me that I'll use frequently enough to warrant my keeping it.
— Alexander Torrenegra (@torrenegra) February 13, 2024
For Carter Gibson, a senior manager working on community management and moderation at Google, it’s the finer details. Things like futzing around with windows and file management are productivity deal-breakers.
“It’s difficult to multitask between ‘windows’,” Gibson told me in an exchange on Threads. “Several file types simply aren’t supported on the Vision Pro. I also can’t see how creating a slide in the VP would be less energy than doing so w/ mouse and keyboard — even if does feel like you’re in Minority Report.”
It’s hard to say how this vocal subset of early adopters will impact the Vision Pro going forward. Many folks who said they’d be returning the device also noted they’d be eager to try a second-gen Vision Pro. Others emphasized that the tech wasn’t the issue at hand so much as the lack of a killer app or comfort. It’s also hard to say how widespread of a phenomenon this is. While these users are speaking out on social media, we have no idea of the actual return rate — or what Apple’s internal expectations for the Vision Pro are.
Read more of this story at Slashdot.
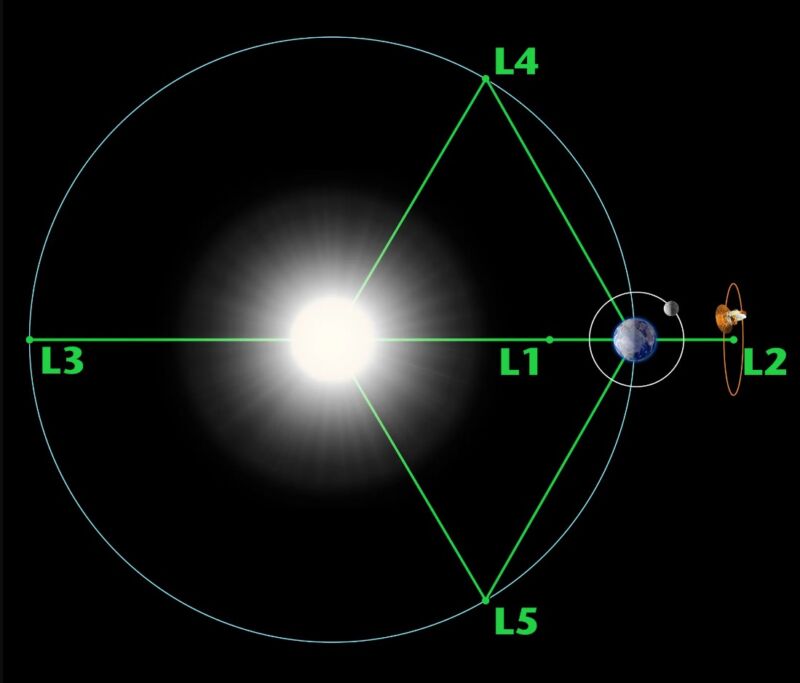
Enlarge / Lagrange points are positions in space where the gravitational forces of a two-body system like the Sun and Earth produce enhanced regions of attraction and repulsion. (credit: NASA)
A bipartisan committee in the US House of Representatives recently issued a report on the economic and technological competition between the United States and China and offered nearly 150 recommendations to "fundamentally reset" the relationship.
The report followed a year-long study of the competition between the countries since China's entry into the World Trade Organization in 2001.
"The Chinese Communist Party has pursued a multi-decade campaign of economic aggression against the United States and its allies in the name of strategically decoupling the People’s Republic of China from the global economy, making the PRC less dependent on the United States in critical sectors, while making the United States more dependent on (China)," the report states.